How to exploit Server-Side Request Forgery (SSRF) vulnerabilities, allowing you to access internal server resources.
https://tryhackme.com/room/ssrfqi
Task 1 What is an SSRF?
A vulnerability that allows users to modify server requests to get access to files or information that they shouldn’t have access to.
Types of SSRF
There are two types of SSRF vulnerability; the first is a regular SSRF where data is returned to the attacker’s screen. The second is a Blind SSRF vulnerability where an SSRF occurs, but no information is returned to the attacker’s screen. What’s the impact?
A successful SSRF attack can result in any of the following:
- Access to unauthorised areas.
- Access to customer/organisational data.
- Ability to Scale to internal networks.
- Reveal authentication tokens/credentials.
Task 2 SSRF Examples
Viewing the site takes us through some examples and shows us how to take advantage of simple SSRF. Using the url we are looking for and ending it with & will give us our flag.
Task 3 Finding an SSRF
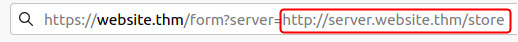
Here we see we can spot SSRF Vulns when we can see a full URL is a parameter in the address bar (pic below):
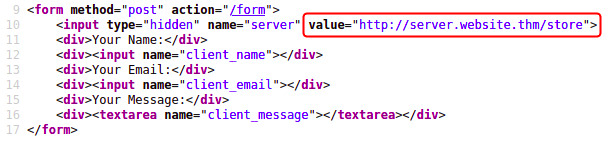
Or hiding in a form field:
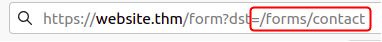
Or a partial URL or a path in the URL
We are also told that these examples are easiar to exploit than others, and will require a lot of trial and error to find a payload that works.
Also if we are trying to access blind SSRFs (SSRF Requests that cannot be seen or is not reflected back to us), we will need to use external tools like requestbin.com, or our own HTTP server like Burp Suites Collaborator Client.
Answer the questions below:
What website can be used to catch HTTP requests from a server?
Requestbin.com
Task 4 Defeating Common SSRF Defences
This task goes over the common approaches that developers aware of SSRF vulerabilities take to protect their servers. Two approaches, deny, or allow lists.
Deny List
A Deny List is where all requests are accepted apart from resources specified in a list or matching a particular pattern. A Web Application may employ a deny list to protect sensitive endpoints, IP addresses or domains from being accessed by the public while still allowing access to other locations. A specific endpoint to restrict access is the localhost, which may contain server performance data or further sensitive information, so domain names such as localhost and 127.0.0.1 would appear on a deny list. Attackers can bypass a Deny List by using alternative localhost references such as 0, 0.0.0.0, 0000, 127.1, 127...*, 2130706433, 017700000001 or subdomains that have a DNS record which resolves to the IP Address 127.0.0.1 such as 127.0.0.1.nip.io.
Also, in a cloud environment, it would be beneficial to block access to the IP address 169.254.169.254, which contains metadata for the deployed cloud server, including possibly sensitive information. An attacker can bypass this by registering a subdomain on their own domain with a DNS record that points to the IP Address 169.254.169.254.
Allow List
An allow list is where all requests get denied unless they appear on a list or match a particular pattern, such as a rule that an URL used in a parameter must begin with https://website.thm. An attacker could quickly circumvent this rule by creating a subdomain on an attacker’s domain name, such as https://website.thm.attackers-domain.thm. The application logic would now allow this input and let an attacker control the internal HTTP request.
Open Redirect
If the above bypasses do not work, there is one more trick up the attacker’s sleeve, the open redirect. An open redirect is an endpoint on the server where the website visitor gets automatically redirected to another website address. Take, for example, the link https://website.thm/link?url=https://tryhackme.com. This endpoint was created to record the number of times visitors have clicked on this link for advertising/marketing purposes. But imagine there was a potential SSRF vulnerability with stringent rules which only allowed URLs beginning with https://website.thm/. An attacker could utilise the above feature to redirect the internal HTTP request to a domain of the attacker’s choice.
Answer the questions below
What method can be used to bypass strict rules? Open Redirect
What IP address may contain sensitive data in a cloud environment? 169.254.169.254
What type of list is used to permit only certain input? Allow List
What type of list is used to stop certain input? Deny List
Task 5 SSRF Box
Time to put what we learned to use in a fictional scenario.
We know a few things:
- Two endpoints we found during content discovery
- /private - which gives us an error message explaining we cant view the page with our IP address
- /customers/new-account-page - has a feature that allows customers to choose an avatar for their account
We are givin the steps to complete this task. By viewing the source and seeing that the hidden fields are actually calling a URL and editing that element to “x/../private” we can call our flag and decode the base64 format to get the answer below.
Answer the questions below
What is the flag from the /private directory?
THM{YOU_WORKED_OUT_THE_SSRF}