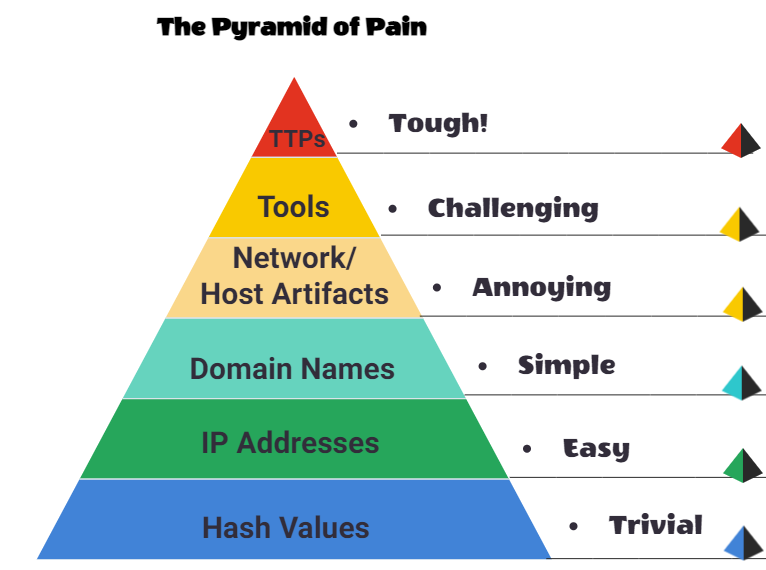
The Pyramid of pain visualizes the level of difficulty it will cause for an adversary to change the indicators associated with them, and their attack campaign.
Hash Values (Trivial)
A hash is the result of a hashing algorithm. A hash value is a unique value that identifies data. Some of the most common hashing algorithms are:
- MD5 (Message Digest) - Designed in 1992 and is a widely used cryptographic hash function with a 128-bit hash. NOT considered cryptographically secure. Vulnerable against a number of attacks including hash collision. Hash collision is when two different input values create the same hash. This can be used by an attacker to create a rogue version of the hash and use that hash to gain access to the legitimate file with the same MD5 hash.
- SHA-1 (Secure Hashing Algorithm 1) - Was designed by the bad guys at the NSA. of couse they build backdoors into algorithm just like the CIA did. It’s not secure and banned for its use now because it’s succeptable to brute force attacks.
- SHA-2 (Secure Hashing Algorihm 2) - Designed by the NIST and the NSA (uh-oh) to replace SHA-1. It has lots of variants, the most comming being SHA-256. The SHA-256 algo returns a hash value of 256-bits as a 64 digit hexadecimal number.
Like we said before about MD5 - a hash is not considered to be cryptographically secure if it two files are able to have the same hash value or digest. The main difference between a hash digest and a hash value is that a digest is the output of a specific hashing algorithm, while a hash value can be generated by any hashing algorithm.
You can use the hash values of files to determine if the file is malicious as they are unique.
We can use online tooks to do hash lookups, such as:- VirusTotal, and Metadefender Cloud - OPSWAT.
Now as we can see its pretty easy to determine if a file is malicious or not if we have its hash right? Wrong. It is trivial for an attacker to modify malware if they know what they are going and they can easily modify just a character in the code to produce a new hash value, which makes threat hunting using file hashes a very difficult task.
IP Address (Easy)
IP addresses are used to identify any decive connected to any network. From a defenders standpoint knowing where the malicious attacks are coming from is super valuable. If we have an IP address we can block, drop, or deny requests from them via a firewall. This tactic only works until the attacker can find another IP address and an experienced attacker has no trouble getting a new one.
One way an attacker can make it challenging for a defender to successfully IP block is by using Fast Flux.
Fast Flux is a DNS technique used by botnets to hide phishing, web proxying, malware delivery and malware communication by hiding behind compromised hosts acting as proxies. The purpose of using Fast flux is to make the communication between malware and command and control centers challenging to be discovered by the SOC.
The concent of fast flux is having many different IP addresses that are associated with a domain name which is constantly changing.
Domain Names (Simple)
Domain names are a little harder for an attacker to change as they will have to purchase new domain, register it, then modidy the DNS records. Also because DNS providers care more about money then security they have loose standards and supply APIs which make it fairly easy and fast for an experienced attacked to change the domain.
Attackers can use a few tricks to hide their domain names from the uninformed. They can use Punycode to redirect users to a malicious domain name that looks legitimate at the first glance. For example a URL that looks like adıdas.de will actually take you to http://xn--addas-o4a.de/
To detect malicious domains we can check proxy or server logs.
Attackers can also hide their domains using URL Shorteners, such as:
- bit.ly
- goo.gl
- ow.ly
- s.id
- smarturl.it
- tiny.pl
- tinyurl.com
- x.co
You can see where the shortened link will send you by appending “+” to it. Ex: goo.gl/mcvc4mc+ or bit.ly/mvJm43+
Host Artifacts (Annoying)
At the upper part of the pyramid attackers will be getting more and more annoyed if we can detect these attacks. If we can detect at this level the attacker will need to go back to their previous steps and change their attack tools and methods. This can be time-consuming for the attacker.
Host artifacts are traces or observables that the attackers have left on the system, like registry values, sus process executions, IOCs (Indicators of Compromise), files, or anything releated to the threat.
So a suspicious process execution followed by a series of strange events would be a good sign that we have come accross some host artifact.
Network Artifacts (Annoying)
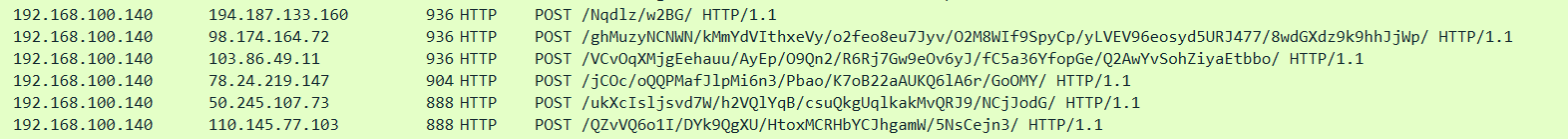
Network artifacts can be user-agent strings, Command and Control information or URI patterns followed by HTTP Post requests. You might see user-agent strings that look strange or havent been observed in your logs before. The user-agent is defined by RFC2616 as the request-header field that contains information about the user-agent making the request.
We can detect network artifacts in Wireshark PCAPs by using network protocol analyzers like TShark or by checking our IDS (Intrusion Defence System) logging from a source like Snort.
An example showing an HTTP POST request containing suspicious strings:
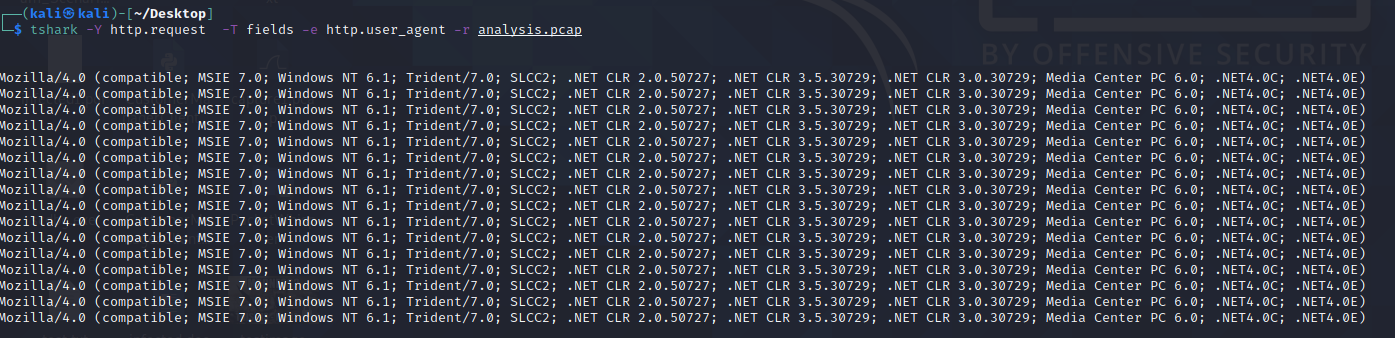
Using TShark command to filter out the User-Agent strings:
1
tshark --Y http.request -T fields -e http.host -e http.user_agent -r analysis_file.pcap
The above are common user-agent strings used by the Emotet Downloader Trojan.
If you can detect these attacks you might be able to block them creating more obstacles for the attacker and make their attemps to compromise the network more difficult.
Tools (Challenging)
We have levelled up our detection capabilities against the artifacts. The attacker would most likely give up trying to break into your network or go back and try to create a new tool that serves the same purpose. It will be a game over for the attackers as they would need to invest some money into building a new tool (if they are capable of doing so), find the tool that has the same potential, or even gets some training to learn how to be proficient in a certain tool.
Attackers would use the utilities to create malicious macro documents (maldocs) for spearphishing attempts, a backdoor that can be used to establish C2 (Command and Control Infrastructure), any custom .EXE, and .DLL files, payloads, or password crackers.
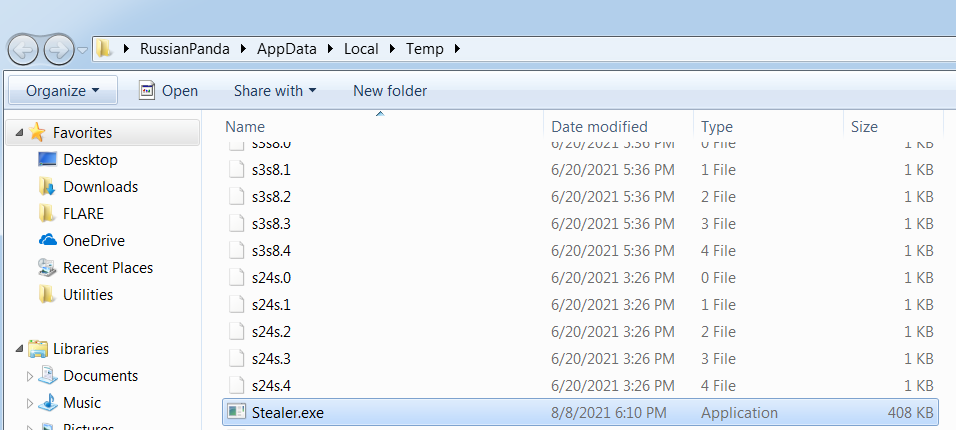
A trojan dropping a suspicious exe in the temp folder
The executions of the suspicious binary
We can use antivirus signatures, detection rules and YARA rules as weapons against attackers at this stage.
YARA is a tool that allows users to create descriptions, or “rules,” of malware and other malicious files based on their characteristics, such as file name, size, and data strings. These rules can then be used to scan files and determine if they match any known malware.
MalwareBazaar and Malshare are good resources to provide you with access to the samples, malicious feeds, and YARA results - these all can be very helpful when it comes to threat hunting and incident response.
For detection rules, SOC Prime Threat Detection Marketplace is a great platform, where security professionals share their detection rules for different kinds of threats including the latest CVE’s that are being exploited in the wild by adversaries.
Fuzzy hashing (Context Triggered Piecewise Hash or CTPH) is also a strong weapon against the attacker’s tools. Fuzzy hashing helps you to perform similarity analysis - match two files with minor differences based on the fuzzy hash values. One of the examples of fuzzy hashing is the usage of SSDeep; on the SSDeep official website, you can also find the complete explanation for fuzzy hashing.
Example of SSDeep from VirusTotal
TTPs (Tough)
The apex of the pyramid.
TTPs are Tactics, Techniques and Protocols, as described by the MITRE ATT&CK Matrix. Which is all the steps the adversary takes to achieve their goals, starting from phising attemps to persistance to data exfiltration.
If we can detect and respons to the TTPs quickly, they have amost no chance to fight back and will have to stat of right from the bottom of the pyramid. If we can detect a Pass-the-Hash attack using Windows Event Log Monitoring and remediate it, we can find the compromised host pretty quickly and stop pivoting inside the network. They would then have to go back, reconfigure their customer tools or give up and try another, easiar target.
Conclusion
We’ve learned the concept of the Pyramid of Pain.
You can pick any APT (Advanced Persistent Threat Groups) as another exercise. A good place to look at would be FireEye Advanced Persistent Threat Groups. When you have determined the APT Group you want to research - find their indicators and ask yourself: “ What can I do or what detection rules and approach can I create to detect the adversary’s activity?”, and “Where does this activity or detection fall on the Pyramid of Pain?”
Source(s): https://tryhackme.com/room/pyramidofpainax